WhoisXML API Now Offers 6 Files for its DNS Database Download Service
WhoisXML API made its DNS database download available in six different files, each for different DNS record types. Doing so makes the DNS database files easier to integrate and analyze and enables particular use cases.
The resource records you can download as database files are:
- A records: An A record directs a domain or subdomain to an IP address. It is possibly the most basic type of DNS record, as all domains should resolve to an IP address to become accessible.
- Mail exchanger (MX) records: This type of record specifies the mail server where email messages meant for a specific domain are accepted.
- Nameserver (NS) records: The NS record determines the authoritative DNS server for the domain name.
- Text (TXT) records: This type of DNS record was initially allotted for human-readable information about a domain that serves as notes for administrators. Its use has, however, evolved to include serial numbers, codes, and server names.
- Canonical name (CNAME) records: A CNAME allows website administrators to provide aliases to domain names by pointing them to another domain. The domain blog[.]example[.]com, for example, can be given the alias or CNAME example[.]com.
- Start of Authority (SOA) records: SOA records contain administrative details about a particular domain’s zone. This record helps manage zone transfers and contains the primary nameserver, serial numbers, and timestamps.
This tutorial looks into the six types of DNS databases now available for download.
How to Access DNS Database Download
Accessing WhoisXML API’s DNS databases requires a subscription. To get started, contact us or send an email to [email protected]. If you already have an account, follow the steps below.
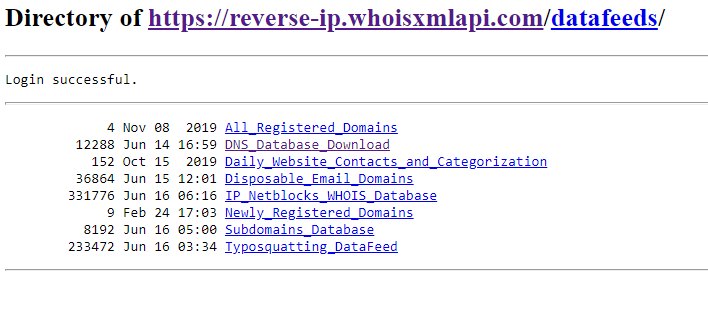
- Go to https://reverse-ip.whoisxmlapi.com/database.
- Click the “Order database” button.
- On the list of subscribed data feeds that appears, select DNS Database Download.
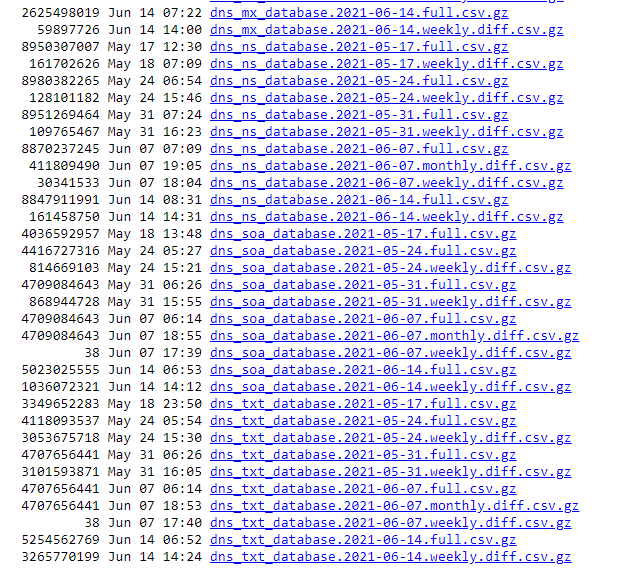
- Select the type of DNS database you want to download. Clicking on a specific file name automatically starts the download.
Understanding the File Naming Conventions
The databases follow this file naming format: dns_[record type]_database.[date].[file type].csv.gz where:
- Record type: Refers to the resource record found in the database, such as A, SOA, TXT, NS, MX, or CNAME. For the DNS A Database, this field is left blank, so the name becomes dns_database.
- Date: The date when the file was generated.
- File type: This field could be “full,” which means you will be downloading the entire database, regardless of date. It could also be “weekly.diff” or “monthly.diff,” which means it only contains the new records found within the week or month specified.
DNS Databases Available from WhoisXML API
The six types of DNS databases we offer are discussed in detail below. More information can also be found here.
DNS A Database
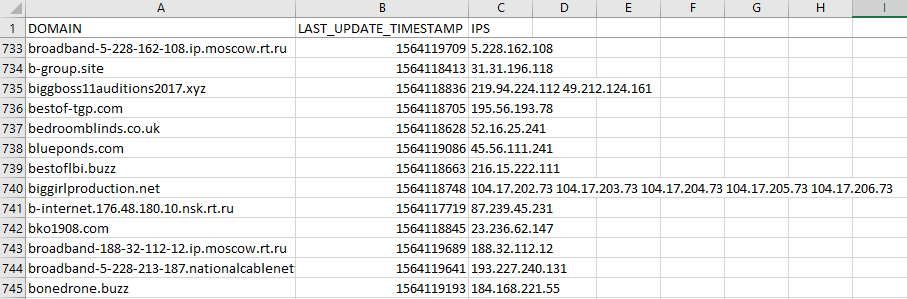
Our DNS A Database contains the IP resolutions of domain names. These files are labeled “dns_database” on the main download page. The database has three columns, namely:
- d: Lists all domain names.
- du: The date and timestamp when the DNS record was last updated.
- ips: The IP addresses the domains resolve to. If a domain resolved to multiple IP addresses in the past, all these IP addresses are reflected in this column.
DNS MX Database
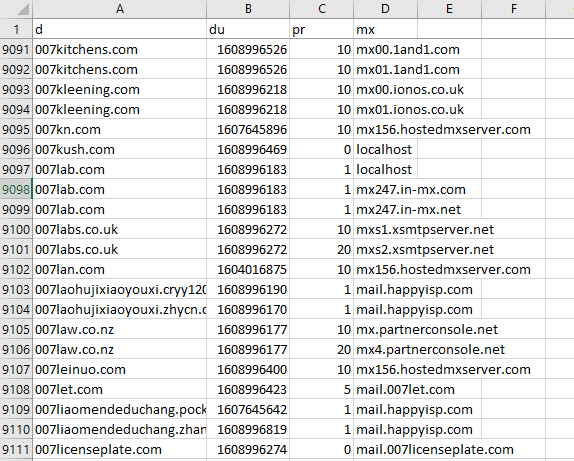
DNS MX Database lists domain names and their corresponding mail servers. The file names for this database type begins with “dns_mx_database,” and has four columns:
- d: This column contains the domain names found for the selected date.
- du: The date and timestamp when the MX record was last updated is reflected here.
- pr: This refers to the priority or preference in which the specific mail server should be used, 1 being the highest priority and 100, the lowest. Setting mail server priority enables load sharing between primary and backup mail servers.
- mx: This column lists the mail server associated with the domain name.
DNS NS Database
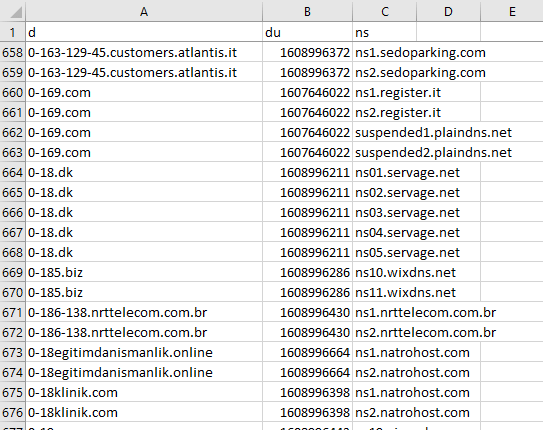
This type of DNS database download helps you map out the NSs associated with a particular domain name. The file names begin with “dns_ns_database,” and contain three columns:
- d: Lists all domain names.
- du: Contains the date and timestamp of the last update made.
- ns: This column includes the NSs associated with the domains listed in the first column.
DNS TXT Database
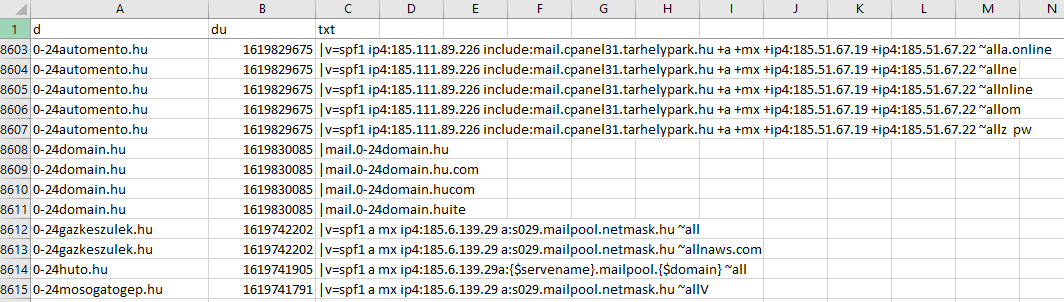
TXT records contain text information about the domain and may serve several purposes, including domain ownership verification and spam prevention. Our DNS TXT Database (signified by the string “dns_txt_database” in their names) has three columns, namely:
- d: This column lists the domain names.
- du: This refers to the date and timestamp when the TXT record was last updated.
- txt: Contains the TXT record detail specified by the domain administrator. If a domain has multiple TXT records, each one is displayed in a different row.
DNS CNAME Database
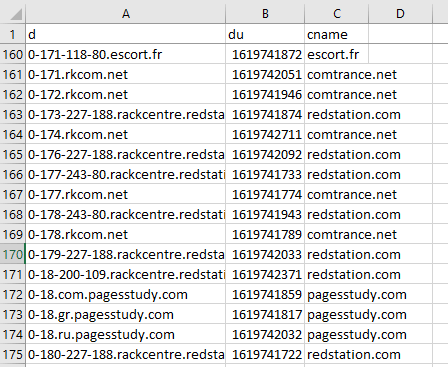
Website administrators can make multiple domains and subdomains point to the same application or page within the same server by setting up CNAME records. Our DNS CNAME Database keeps track of such records to help you see which domains have CNAME records and what domains they point to.
This type of database has the string “dns_cname_database” in their names and has three columns:
- d: This column lists all domain names.
- du: Contains the date and timestamp when the CNAME record was last updated.
- cname: Lists the domain that the corresponding domain identified in the first column points to.
DNS SOA Database
This type of database contains the SOA records of domain names that contain administrative details about the zone. File names start with “dns_soa_database,” and files have three columns:
- d: Refers to the domain names in the database.
- du: This column contains the date and timestamp when the SOA record was last updated.
- soa: Lists the SOA record associated with the domain indicated in the first column.
DNS Databases in Action: What Attacks Can They Help Prevent?
DNS Hijacking
DNS hijacking or redirection is a type of DNS attack where malicious actors change the victims’ DNS settings to redirect them to malicious websites or applications. One example of malware that makes DNS hijacking possible is DNSChanger, which can replace a domain’s NS with one that points to a malicious IP address.
DNS databases, specifically DNS NS and A Databases, can help you check which domains have possibly been redirected to malware-carrying IP addresses and NSs.
Malware
Aside from DNS hijacking, threat actors very often use malware, including ransomware, to carry out attacks. Changing the DNS settings of a victim’s computer may enable threat actors to plant data-stealing and -locking malware on their systems.
With a DNS database, security teams can check for domains that resolve to IP addresses associated with ransomware and other malware. For example, in the sample DNS A Database, three domains point to 50[.]63[.]202[.]39, an IP address cited for its involvement in ransomware and other malicious campaigns. These domains are:
- alextandang[.]com
- celltechsvcs[.]com
- youngswagclothes[.]com
The timestamps on the database can provide more context on associations between domains and the malicious IP address.
Spam Campaigns and Email Spoofing
TXT records can be used to enhance email security by making it a space for specifying Sender Policy Framework (SPF) records and Domain-Based Message Authentication, Reporting, and Conformance (DMARC) authentication. Blank TXT records or unspecified SPF records can make a domain vulnerable to spoofing and cause emails to be marked as spam.
---
We will continue to make our DNS database download services available in easily accessible and consumable formats. Our goal is to help cybersecurity teams, investigators, and researchers identify threats, uncover artifacts, and map out associations between malicious records.




































